New Gmail Phishing Scam Exploits Google’s Own Tools
Click here to view/listen to our blogcast.
In a disturbing new trend, cybercriminals have found a way to exploit trusted Google services to launch highly convincing phishing attacks — and if you use Gmail, you could be at risk.
What’s Happening?
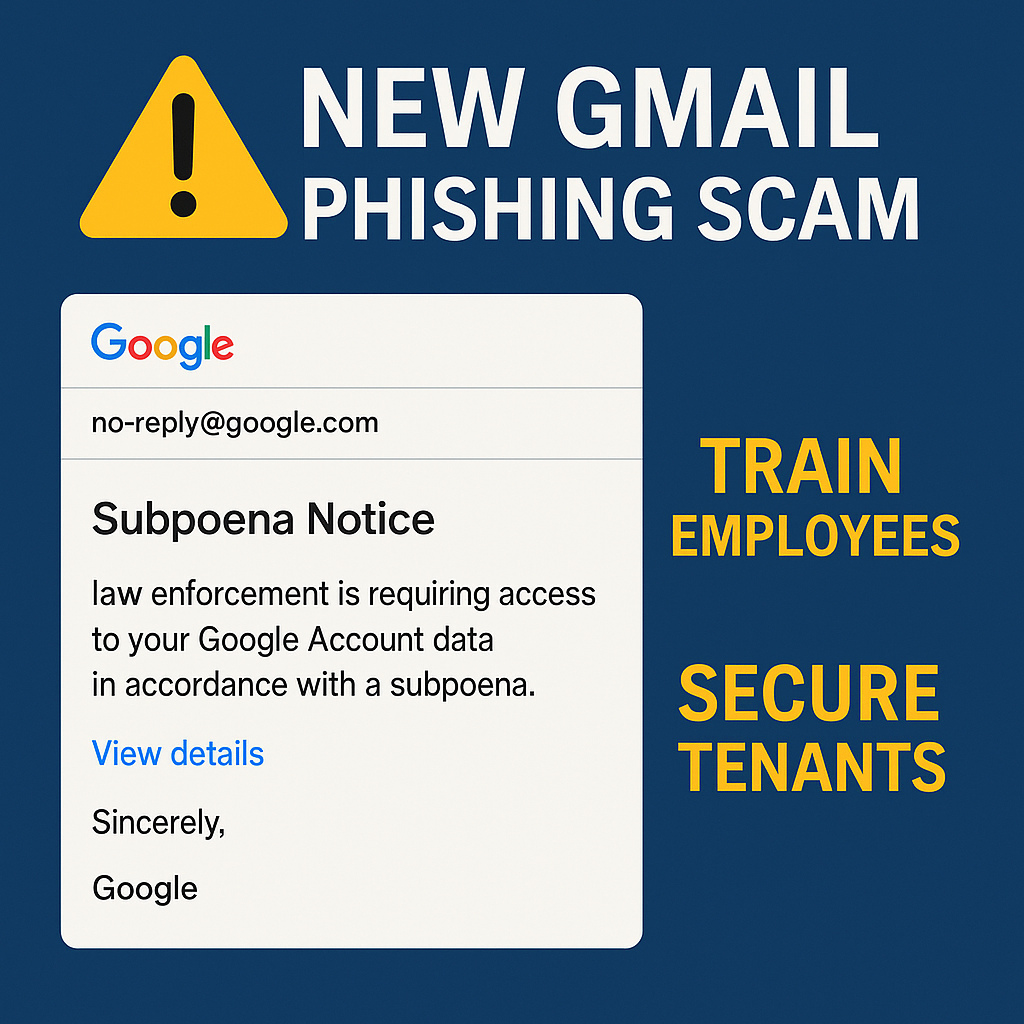
Attackers are sending out emails that appear to come from the official address “[email protected]”, a source most people would immediately trust. These emails claim that law enforcement has issued a subpoena for access to your Google Account. They pressure you to click a link to review or respond to the alleged legal request.
But here’s the catch: it’s a scam. The attackers are not merely spoofing Google’s branding — they’re abusing Google’s own platforms, like Google Sites, to create authentic-looking emails and webpages.
How Are They Bypassing Security?
This phishing campaign cleverly evades some of Gmail’s normal security checks, including DKIM (DomainKeys Identified Mail), a system designed to verify the authenticity of emails.
The attackers exploit a loophole by embedding their malicious phishing content into the app name field of a legitimate Google tool. Because Google autofills information from its own trusted infrastructure, the scam emails appear to come from Google’s actual servers — making them much harder for traditional spam filters to detect.
When a user clicks the link provided, they are sent to a well-crafted fake webpage, often hosted on a Google Sites page, prompting them to enter their Google credentials or other sensitive information.
Why This Scam Is So Dangerous
- It looks legitimate: Because the email technically comes from Google’s servers, even advanced users might not notice anything suspicious at first glance.
- It abuses trust: Most people inherently trust emails from Google, making them more likely to act without thinking critically.
- It bypasses common security alerts: Traditional phishing red flags like “this message failed authentication” warnings don’t appear.
What You Should Do
Here’s how to protect yourself:
✅ Be Skeptical of Urgent Messages: If you receive a sudden legal warning, especially one demanding immediate action, take a step back.
✅ Don’t Click Links in Suspicious Emails: Instead, navigate to your Google Account directly by typing https://myaccount.google.com into your browser.
✅ Verify Directly With Google: If you’re concerned about a legal request or subpoena, log into your Google account and check your security or notifications panel – Google will post important legal notices there.
✅ Use Multi-Factor Authentication (MFA): Even if someone captures your password, MFA can stop them from accessing your account.
✅ Report Suspicious Emails: Forward suspicious Gmail messages to [email protected].
Final Thoughts
This new phishing attack highlights a critical truth: technology alone isn’t enough. Even when using trusted platforms like Google, human error remains the biggest vulnerability. That’s why security awareness training is so vital – your first line of defense is an informed and cautious user.
But training alone isn’t enough either. If an attacker does succeed in stealing credentials, the damage can spread across your entire email environment. That’s why tenant-level email security protections — such as multi-factor authentication (MFA), login anomaly detection, privileged account protection, and suspicious activity alerts – are essential.
🤝 CDML is Here To Help!
At CDML Computer Services, we help our clients defend themselves on both fronts:
- We train your employees to spot and avoid scams like this.
- We secure your Google Workspace or Microsoft 365 tenant to limit damage if a breach occurs.
If you’d like a review of your current email security setup or want to roll out security training for your employees, reach out to us today. Proactive steps now can prevent devastating breaches later.
Stay smart, stay protected – we’re here to help.
📞 Contact us here: https://cdml.com/contact/
📚 Read more on our blog: https://cdml.com/blog-2
📺 Listen to our blogcasts: https://www.youtube.com/@CDMLComputerServices